In 2016, NSF awarded us a grant to examine the security of heavy vehicle networks, such as semi-trucks. Working with Dr. Daily, who created heavy vehicle network and component simulators, we created an interface and attack vectors of heavy vehicles. The testbed allows other researchers to perform their own attacks and test the security of heavy vehicle CAN networks, with a mix of real parts from a semi-truck and sensor simulators to simulate real conditions faced by heavy vehicles. The testbed can be extended to other systems which use CAN, such as building automation, medical devices, and manufacturing.
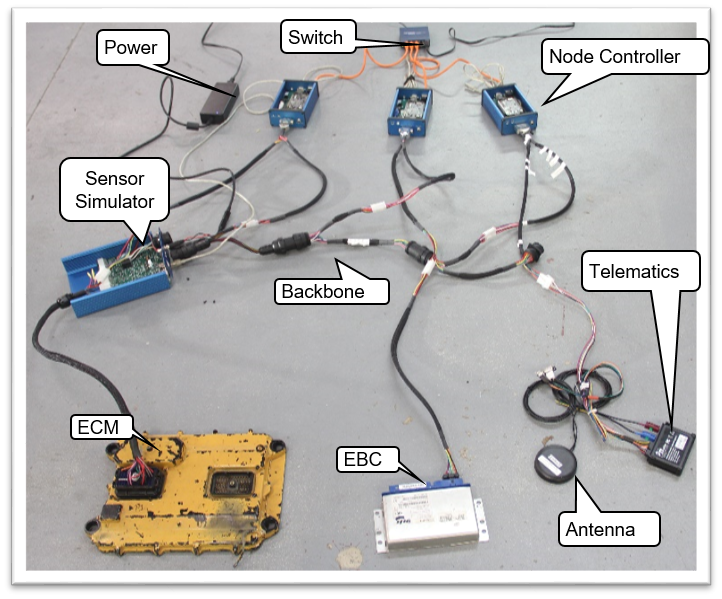
The testbed consists of a web interface for remote users to design and schedule experiments, stored data from previous experiments, and a direct connection to devices, such as an Engine Control Module, Electronic Brake Controller, a telematics device, and the sensor simulator. Using the testbed, we have demonstrated Denial-of-Service attacks using CAN data-link layer requests and connection management protocols.
Citation
- J. Daily, R. Gamble, S. Moffitt, C. Raines, J. Miran, I. Ray, S. Mukherjee, H. Shirazi (2016). Towards a Cyber Assurance Testbed for Heavy Vehicle Electronic Controls. International Journal of Commercial Vehicles (Society of Automotive Engineers). 9 (2), 339. DOI: https://doi.org/10.4271/2016-01-8142.
- S. Mukherjee, H. Shirazi, I. Ray, J. Daily, and R. Gamble (2016). Practical DoS Attacks on Embedded Networks in Commercial Vehicles. International Conference on Information Systems Security (ICISS DOI: https://doi.org/10.1007/978-3-319-49806-5_2
Acknowledgement
This material is based upon work supported by the National Science Foundation under Grant No. 1619641 and Grant No. 1619690. This work was partially sponsored by National Motor Freight Traffic Association, Inc. (NMFTA).