A resilience system automatically adapts to a situation that impedes its mission. If an autonomous system adapts to achieve mission success and that adaptation is crafted at runtime, then confidence in its continued compliance with functional and security requirements must be established. Traditional assurance techniques, such as testing and formal analysis of system reconfiguration (e.g., via code repair or reused code), are typically not applicable at runtime given performance constraints. Moreover, for security threats, determined as part of system situational awareness, the expected level of confidence must be coupled with defensive resilience.
Security Assurance for Adaptive System
Maintaining a high level of confidence in guaranteeing requirement compliance while defending against security threats in an autonomous system poses multiple research challenges. Security certification is a highly manual effort that documents the process and artifacts for a system to provide security compliance guarantees. When the system configures a new component, patch, or decision-making strategy at run time, there can be direct and propagated impact on security compliance. Thus, these run-time adaptations must be risk-assessed against both functional and security requirements. Prior work in this area must be extended to accommodate new system designs that embed adaptation and security frameworks, so that the adaptations can be holistically examined from architectural, verification and validation (V&V), and certification and accreditation (C&A) perspectives. Another challenge is pinpointing and alerting to the effect of the adaptation on the system architecture as it relates to the assurance of mission requirements and security constraints. The functional behavior of the system must be codified separately from and prior to its deployment into the system to enable trustworthiness and risk assessments.
We have developed a framework to express, codify, and automatically maintain operational system security assurance cases (SACs) for autonomous systems that are reconfiguring at runtime to achieve mission objectives resiliently and securely in the face of adverse conditions.
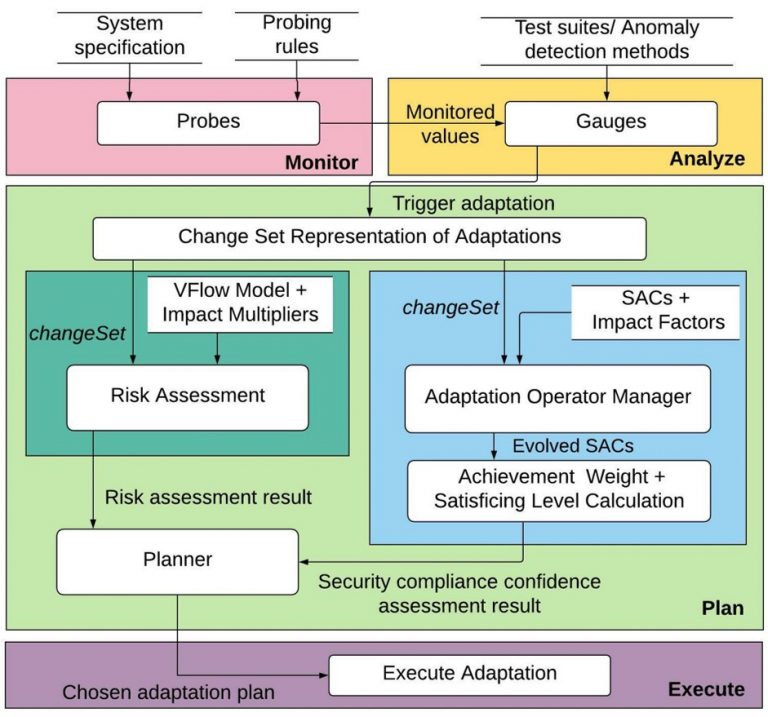
Assurance cases have been accepted as a means for certifying the utility and satisfaction of trustworthiness, safety, and mission objectives. SACs will capture the trustworthiness and risk assessment chain of evidence from initial development through system evolution during run-time adaptation in response to environmental and system uncertainty with respect to security threats. Given the dynamic updates to the physical and cyber aspects of the system functionality due to its interaction with the environment, we envision that the SACs will need dynamic updating to reflect the changing security conditions. In turn, security mitigations due to attacks or detected vulnerabilities may trigger subsequent system adaptations. We explicitly address the dual and interacting dynamic updates of the autonomous system and the supporting SACs, with respect to system resilience, risk management, and assurance traceability.
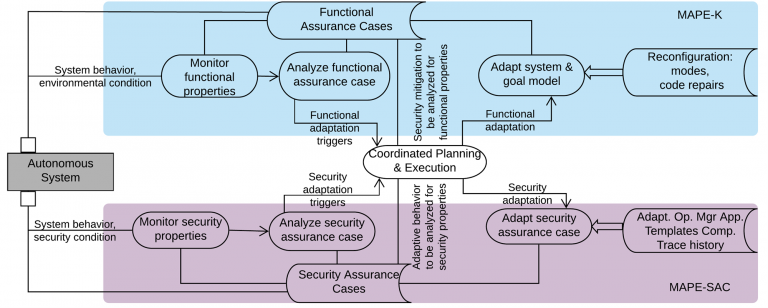
Given the complexity and independent properties of the prior efforts on monitoring, planning, and risk assessment, our research supports the need to design technology for integration, so that the model transformation and translation effort is reduced, while the implementation efficiency and adaptation traceability are increased. A key innovation of this research is the MAPE-SAC loop, inspired by the MAPE-K loop that serves as the foundation for the feedback loop to manage autonomous systems. Both loops involve the monitor, analyze, plan, and execute steps, differing only in the target of adaptation. For MAPE-K, the target is the autonomous system. For MAPE-SAC, the target is the collection of SACs.
Adaptations may be triggered by environmental changes (e.g., road conditions, sensor failures, etc.) and/or cyber threats (e.g., denial of service attacks, compromised data, etc.). The MAPE-K/MAPE-SAC framework to ensure that functional and security properties are satisfied.
Citation
- Extending Context Awareness by Anticipating Uncertainty with Enki and Darjeeling, S. Jahan, I. Riley, C. Walter, R. Gamble, 5th Workshop on Self-Aware Computing, pp. 170-175, 2020. doi: 10.1109/ACSOS-C51401.2020.00051.
- MAPE-K/MAPE-SAC: An interaction framework for adaptive systems with security assurance cases, S. Jahan, I. Riley, C. Walter, R. Gamble, M. Pasco, P. K. McKinley, B. H. C. Cheng, Future Generation Computer Systems, Vol. 109, pp. 197-209, March 2020. https://doi.org/10.1016/j.future.2020.03.031
- MAPE-SAC: A Framework to Dynamically Manage Security Assurance Cases, S. Jahan, M.W. Pasco, R.F. Gamble, P.K. McKinley, and B.H.C. Cheng, 6th Int’l Wksp on Self-Improving System Integration, June 2019.