Verification Awareness
Self-adaptive and self-repairing systems pose a serious challenge to the sustainable verification of a software system. Any system that has been verified must be re-verified when an adaptation is deployed. Re-verification cannot be performed at runtime in most cases, as often there are formal requirements specified at design time that cannot be violated. Also, there is no set method of confirming that an adaptation will not violate a requirement at some state in the future. Thus, there is a need to evaluate expected states of a system and how the adaptation will impact those states for a verified system to continue operating after self-adapting or self-repairing.
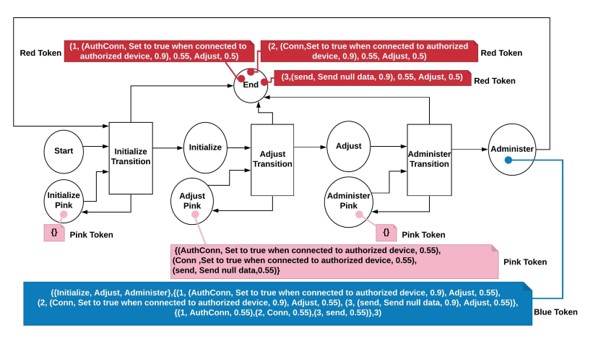
Our work focuses on the creation of a verification workflow using Petri Nets. A Colored Petri Net (CPN) is embedded within the system operations, providing a software architecture awareness. When a system needs to adapt at runtime, it can simulate its proposed changes through verification workflow (VFlow) using its critical requirements to determine a) if the plan will potentially violate a requirement and b) how the changes can negatively propagate through system execution. If a plan is determined to be a risk to a requirement violation, a risk token used in the verification workflow is associated with each adaptation detailing risk level and architecture placement. Choice of adaptation is based on the least risk to requirement violation but essential for mission success.
Citation
- Evaluating Verification Awareness as a Method for Assessing Adaptation Risk, I. Riley, S. Jahan, A. Marshall, C. Walter, R. Gamble, Future Generation Computer Systems, Vol. 119, pp. 110-135, ISSN 0167-739X, 2021, doi:https://doi.org/10.1016/j.future.2021.01.034
- Assessing Adaptations based on Change Impacts, S. Jahan, I. Riley, R. Gamble, 1st IEEE International Conference on Autonomic Computing and Self-Organizing Systems, pp. 48-54, 2020. doi: 10.1109/ACSOS49614.2020.00025.
- Toward a Negotiation Framework for Self-Integration, I. Riley, S. Jahan, R. Gamble, 7th Self-Improving Systems Integration Workshop, pp. 95-100, 2020. doi: 10.1109/ACSOS-C51401.2020.00038.
- Evaluating Security Assurance Case Adaptation, S. Jahan, A. Marshall, and R. Gamble, Proceedings of the 52nd Hawaii International Conference on System Sciences, Jan. 2019.
- Self-Adaptation Strategies to Maintain Security Control Assurance Cases, S. Jahan, A. Marshall, and R. Gamble, Proceedings of the 12thIEEE International Conference on Self-Adaptive and Self-Organizing Systems, 2018.
- Toward Evaluating the Impact of Self-adaptation on Security Control Certification, A. Marshall, S. Jahan, and R. Gamble, to appear in the Proceedings of the 13thInternational Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS), May 2018.
- Assessing the Risk of an Adaptation using Prior Compliance Verification, A. Marshall, S. Jahan, and R. Gamble, in the Proceedings of the 51stHawaii International Conference on System Sciences, Jan. 3-6, 2018.
- Adaptive Coordination to Complete Mission Goals, S. Jahan, C. Walter, S. Alqahtani, and R. Gamble, Proceedings of the 5th Workshop on Self-Improving System Integration, Sept. 2018.
- Embedding Verification Concerns in Self-Adaptive System Code, S. Jahan, A. Marshall, and R. Gamble, in the Proceedings of the 11th IEEE International Conference on Self-Adaptive and Self-Organizing Systems, Tucson, AZ, Sept. 2017.
- Visualizing Self-Adaptive Plan Simulations given Embedded Verification Concerns, S. Jahan, A. Marshall, and R. Gamble, in the Proceedings of the11th IEEE International Conference on Self-Adaptive and Self-Organizing Systems (Demo Track), Tucson, AZ, Sept. 2017.
Acknowledgement
The research sponsored by Air Force Research Laboratory, USA under agreement FA8750-16-1-0248.