With the ubiquity and growing computing power of wearables comes an increased need for research into the security of wearable devices. Because wearables are attached to a user’s body, direct access to the device by attackers is difficult. This leaves an attacker with attacking wearables through their Bluetooth connection with their base stations.
The challenge of defending wearables is twofold. First, wearables, while gaining power constantly, are still low-powered devices with relatively small batteries. Each wearable may not be capable of performing complex security calculations without compromising battery life, which would be impactful to the user. Second, consumer wearables are often proprietary, with little to no developer access to the device. This makes it difficult for an attacker to find a weakness directly in the firmware of the device, but also makes it impossible for a developer/researcher to repair any weakness found. The lack of developer access also makes even foundational research difficult when attempting to secure wearable devices.
To that end, we have created a proof-of-concept app for improving the security of wearable devices and their base stations. Our app improves the computing power of individual wearable devices by spreading the computational burden across multiple wearables and the base station, allowing wearables to focus on only the security threats they can themselves detect while operating normally otherwise, allowing more powerful devices to analyze additional threats. We create a fog computing network consisting of wearables, their base stations, and the cloud, dubbed the personal fog, to improve the computing power and ability to secure the wearables and base station communication. We introduce a MAPE-K loop (Monitor, Analyze, Plan, and Execute with a Knowledge base) to allow each device as part of the personal fog to adapt its communication to prevent an attacker from intercepting or changing the messages communicated between fog nodes.
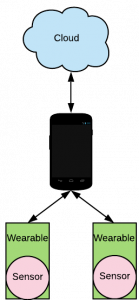
Currently, we limit the adaptation to the following:
- Stop sending data, remain connected (send empty packets)
- Stop sending data, disconnect
These two options can be employed by both wearables and base stations to prevent eavesdropping and Man-in-the-Middle attacks. Additional potential future adaptation options include:
- Sending junk data
- Introduce additional encryption algorithms
However, with the additional computing power of the personal fog, we introduced the concept of fostering between devices. Fostering allows wearables and base stations to communicate between nearby personal fogs to determine if their current environment is secure. This is done through a very specific series of Bluetooth packets. Should any data from the fostering exchange be different from what is expected, the fostered devices will assume it is insecure and choose to adapt.
The introduction leads to two new adaptations based on the original adaptation options:
- Stop sending data, remain connected, allow fostering
- Stop sending data, remain connected, do not allow fostering
- Stop sending data, disconnect, allow fostering
- Stop sending data, disconnect, do not allow fostering
Testbed
Due to the difficulty of implementing the personal fog on existing consumer wearables, we have created a wearable security testbed. The testbed is composed of Raspberry Pi 3s, with one acting as a base station and two acting as wearables. If needed, each base station can connect to up to 8 wearables, as per the Bluetooth standard. Using the testbed allows us to carefully examine the use of the personal fog without the need for consumer devices with developer access. The testbed uses pybluez, a Python library for Bluetooth communication, to send and receive messages between the wearables and the base station.


Citation
- Walter, C. “The Personal Fog: An Architecture for Limiting Wearable Security Vulnerabilities,” Dissertation, The University of Tulsa, 2018
- Walter, C. and Gamble, R.F., “Gait-Based Identification Using Wearables in the Personal Fog,” Proceedings of the 52nd Hawaii International Conference on System Sciences, to appear January 2019.
- Walter, C., Riley, I., and Gamble, R.F., “Securing Wearables through the Creation of a Personal Fog,” Proceedings of the 51st Hawaii International Conference on System Sciences, nominated for Best Paper Award (top 10%), Jan. 2018.
- Walter, C., Riley, I., He, X., Robards, E., and Gamble, R.F., “Toward Predicting Secure Environments for Wearable Devices,” Proceedings of the 50th Hawaii International Conference on System Sciences, nominated for Best Paper Award (top 10%), Jan. 2017. DOI: 10.24251/HICSS.2017.168
- Walter, C., Hale, M.L., and Gamble, R.F., “Imposing Security Awareness on Wearables,” Proceedings of the 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems, p. 29-35, 2016. DOI: http://dx.doi.org/10.1145/2897035.2897038